
Crypto Mining Software Threatens GCP Virtual Servers
What is included in Google's report on typical attacks against cloud systems on Google Cloud Platform (GCP)?
At the end of 2021, Google released its first report on typical threats to cloud users, focusing on the security of Google Cloud Platform. Google Cloud Platform offers enterprise customers multiple scenarios for building cloud systems, from hosting and running individual applications to high-performance computing deployment.
Reasons for attacking Google Cloud Platform instances
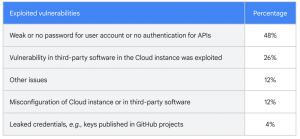
The report analyzes the last 50 successful attacks against private servers or applications, focusing on the causes and consequences of attacks against private GCP instances. 48% of the cases Google analyzed were caused by using a weak password (or no password at all) on server-based accounts. In 26% of cases, hackers exploited a vulnerability in cloud server software. Incorrect server or application configuration led to 12% of cases, while only 4% of cases were due to password or access key leaks.
The second category was based on a mistake not unusual for developers: uploading authentication data along with source code to a public repository on GitHub or a similar service. According to a report by GitGuardian, up to 5,000 “secrets” (API keys, password/username pair, certificates) are uploaded to GitHub every day, and in 2020 there were 2 million such leaks.
Google states that cybercriminals tend not to target specific companies, but instead regularly scans all IP addresses belonging to Google Cloud Platform to look for examples of vulnerabilities. The meaning of this automation is clear: if you make an unprotected server accessible over the internet, the chances of being hacked are almost certain and will likely be hacked soon (in some cases, the attack started within 30 minutes of creating a new instance). Since most hacked servers are involved in illegal operations within half a minute, the time between hacking and the start of malicious activity is even shorter.
Why do attackers prefer Google Cloud Platform instances?
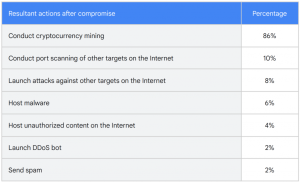
Siber suçlular, hackledikten sonra bulut kaynaklarıyla ne yapıyor? Vakaların büyük çoğunluğunda (%86), sunucuya bir kripto madencilik yazılımı (kripto para birimi oluşturmak için başkalarının kaynaklarını kullanan bir program) kuruldu. En yaygın olarak kritp madencilikte kullanılan kaynaklar CPU/GPU kaynaklarıdır, ancak raporda aynı zamanda boş disk alanından yararlanan Chia kripto para birimi madenciliğinden de bahsediliyor. Vakaların diğer %10’unu oluşturan güvenliği ihlal edilmiş sunucular, yeni kurbanları aramak için bağlantı noktası taraması için kullanıldı. Vakaların %8’inde ise sunucudan diğer ağ kaynaklarına saldırı gerçekleştirildi. Ele geçirilen bulut platformu sunucularının kullanıldığı daha nadir yasa dışı etkinlik türleri arasında şunlar yer alıyor: Kötü amaçlı yazılım, yasak içerik veya her ikisini birden barındırma, DDoS saldırılarını gerçekleştirme ve spam e-posta dağıtımı.
If someone hacks a cloud service and installs cryptomining software, their actions not only damage the customer's reputation and risk access to their own apps or websites, but can also expose victims to massive utility bills in just a few hours.
Recommendations for securing GCP instances
In most cases Google reviewed, users could avoid problems by following minimum security requirements, such as using strong passwords and additional authorization factors, taking due care when uploading source code, and regularly updating installed software to fix known vulnerabilities.
In general, it is necessary to apply the same protection measures for cloud systems as for other types of infrastructure. As a minimum, they need regular audits, monitoring for suspicious activity, and isolating critical data.
A few additional precautions are required for all businesses deploying their infrastructure to public cloud services, not just organizations using Google Cloud Platform. As Google points out, one of the most important of these measures is to set up automatic conditional alerts to determine if resource consumption has exceeded a certain threshold or to detect a rapid increase in costs.
Source: https://www.kaspersky.com.tr/blog/attacks-on-google-cloud-platform/10448/
Sign up for the e-mail list to be informed about the developments in the cyber world and to be informed about the weekly newsletter.


