New Backdoor Targets French Entities via Open-Source Package Installer
Researchers have exposed a new targeted email campaign aimed at French entities in the construction, real estate, and government sectors that leverages the Chocolatey Windows package manager to deliver a backdoor called Serpent on compromised systems.
Enterprise security firm Proofpoint attributed the attacks to a likely advanced threat actor based on the tactics and the victimology patterns observed. The ultimate objective of the campaign remains presently unknown.
"The threat actor attempted to install a backdoor on a potential victim's device, which could enable remote administration, command and control (C2), data theft, or deliver other additional payloads," Proofpoint researchers said in a report shared with The Hacker News.
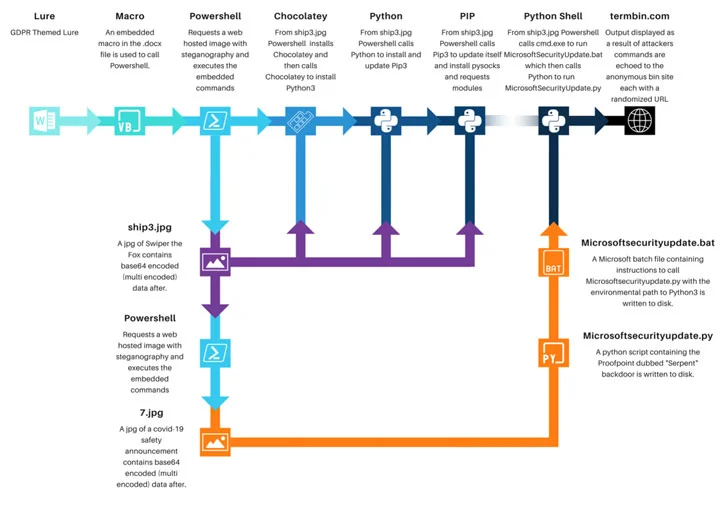
The phishing lure that triggers the infection sequence makes use of a resume-themed subject line, with the attached macro-embedded Microsoft Word document masquerading as information related to the European Union's General Data Protection Regulation (GDPR).
Enabling the macros results in its execution, which retrieves a seemingly harmless image file hosted on a remote server but actually contains a Base64-encoded PowerShell script that's obscured using steganography, a little-used method of concealing malicious code within an image or audio in order to circumvent detection.
The PowerShell script, in turn, is engineered to install the Chocolatey utility on the Windows machine, which is then utilized to install the Python package installer pip, the latter of which acts as conduit to install the PySocks proxy library.
Also retrieved by the same PowerShell script is another image file from the same remote server that includes the camouflaged Python backdoor dubbed Serpent, which comes with capabilities to execute commands transmitted from the C2 server.
In addition to steganography, the use of widely recognized tools such as Chocolatey as an initial payload for follow-on deployment of genuine Python packages is an attempt to stay under the radar and not be flagged as a threat, Proofpoint said.
The attacks have not unearthed associations with a previously identified actor or group, but are suspected to be the work of a sophisticated hacking crew.
"This is a novel application of a variety of technologies that are often legitimately used within organizations," Sherrod DeGrippo, vice president of threat research and detection at Proofpoint, said in a statement.
"It capitalizes on many organizations', specifically technical groups, desire to allow their users to be 'self-sufficient' in regards to self-tooling and package managers. Additionally, the use of steganography is unusual and something we don't see regularly."
Source: https://thehackernews.com/2022/03/new-backdoor-targets-french-entities.html
Sign up for the e-mail list to be informed about the developments in the cyber world and to be informed about the weekly newsletter.