
FBI: Avoslocker Ransomware Targets US Critical Infrastructure
The Federal Bureau of Investigation (FBI) warns of AvosLocker ransomware being used in attacks targeting multiple US critical infrastructure sectors.
This was disclosed in a joint cybersecurity advisory published this week in coordination with the US Treasury Department and the Financial Crimes Enforcement Network (FinCEN).
"AvosLocker is a Ransomware as a Service (RaaS) affiliate-based group that has targeted victims across multiple critical infrastructure sectors in the United States including, but not limited to, the Financial Services, Critical Manufacturing, and Government Facilities sectors," the FBI said [PDF].
"As a result, AvosLocker indicators of compromise (IOCs) vary between indicators specific to AvosLocker malware and indicators specific to the individual affiliate responsible for the intrusion."
The advisory provides network defenders with indicators of compromise (IOCs) they can use to detect and block AvosLocker ransomware attacks.
AvosLocker first surfaced during the summer of 2021, promoting their Ransomware-as-a-Service (RaaS) operation on underground forums and calling for ransomware affiliates to join them.
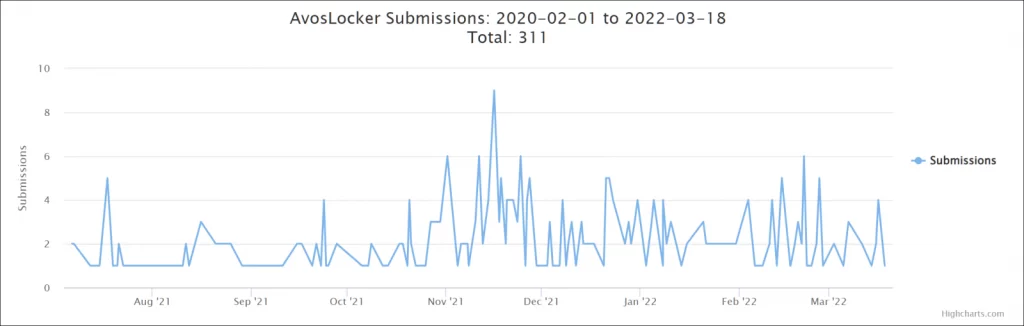
AvosLocker has seen a spike in activity between November and December 2021 and is still constantly hitting and encrypting at least a handful of victims each month based on ID-Ransomware submissions.
The FBI also shared technical details on this RaaS operation, including that AvosLocker representatives allegedly will also call victims to direct them to the payment site to negotiate reduced ransom payments.
If this is true, AvosLocker would be yet another cybercrime group known for using this tactic to push them to pay the ransoms, a tactic pioneered and filed tested by the Sekhmet, Maze, Ryuk, and Conti ransomware gangs.
In some cases, AvosLocker negotiators also threaten and launche distributed denial-of-service (DDoS) attacks during negotiations, likely when the victims are not cooperating, to convince them to comply with their demands.
Mitigation measures to help network defenders prevent AvosLocker ransomware attacks include network segmentation and regular offline backups, as well as keeping software up to date, especially Microsoft Exchange Server, a known attack vector used by AvosLocker affiliates.
Earlier this month, the FBI also revealed that another ransomware gang tracked as Ragnar Locker has successfully breached the networks of at least 52 organizations across ten critical infrastructure sectors as of January 2022.
Sign up for the e-mail list to be informed about the developments in the cyber world and to be informed about the weekly newsletter.


