
Common Spear-Phishing Tricks
To be ready for attacks targeting your company, information security officers need to know about received spear-phishing e-mails.
Virtually every employee of a large company comes across the occasional e-mail aiming to steal their corporate credentials. It’s usually in the form of mass phishing, an attack in which e-mails are sent out at random in the hope that at least some recipients will take the bait. However, the stream of phishing e-mails may contain one or two more dangerous, targeted messages, the content of which has been customized for employees of specific companies. This is spear-phishing.
Spear-phishing messages represent a clear sign that cybercriminals are interested in your company, specifically, and it may not be the only attack in play. That is a major reason infosec officers need to know if any employee has received a spear-phishing e-mail — they need to prepare countermeasures and alert personnel in good time.
That’s why we advise IT to check filtered e-mails periodically in search of spear-phishing, and to teach other employees how to spot signs of targeted phishing. What follows are a few of the most common tricks, with examples from some fresh spear-phishing campaigns.
Misspelled company name
The human brain does not always perceive the whole of a written word — it sees a familiar beginning and completes the rest by itself. Attackers can take advantage of this trait by registering a domain that differs from your company’s by just one or two letters.
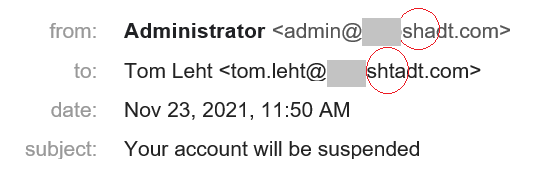
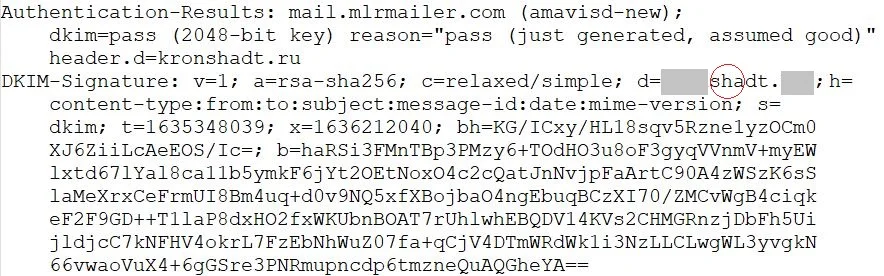
The cybercriminals who own the domain can even set up a DKIM signature so that the e-mail passes all checks — it’s their domain, after all.
Extra words in the company name
Another way to fool recipients into thinking a colleague is at the other end is to register a two-word domain, for example, to appear as a sender from a local branch or a particular department. In the latter case, cybercriminals tend to impersonate tech support or security personnel.
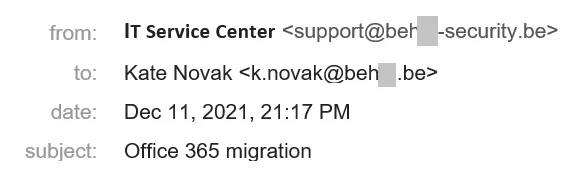
In reality, employees from every department should have a standard corporate e-mail address. No one ever sets up a separate domain for security personnel. As for local offices, if you’re not sure, check the domain in the corporate address book.
Specific content
A phishing e-mail mentioning your company (or worse, the recipient) by name is a sure sign of spear-phishing and a reason to sound the alarm.
Highly specialized topic
Strictly speaking, seeing those names doesn’t always mean a message is spear-phishing — it might be a variation on a mass-phishing scam. For example, phishers may use a database of conference participants’ addresses and play on the topic of the conference — that’s mass phishing. If they try to attack employees of a particular company in the exact same way, however, that’s spear-phishing, and thus security needs to know about it.
Finally, to be able to search for potential spear-phishing signs without diminishing the company’s actual security, we recommend installing protective antiphishing solutions on mail servers as well as on employee workstations.
Source: https://www.kaspersky.com.tr/blog/common-spear-phishing-tricks/10399/
Sign up for the e-mail list to be informed about the developments in the cyber world and to be informed about the weekly newsletter.
Haber bültenine kaydolduğunuz için teşekkürler!
Something went wrong.
We respect your privacy and take protecting it seriously.
Recent Posts
- Attack Surface Management September 5, 2022
- Russian Sberbank Says It’s Facing Massive Waves of DDoS Attacks May 20, 2022
- Windows admins frustrated by Quick Assist moving to Microsoft Store May 15, 2022
- This Week in Cyberspace (19-25 March 2022) March 25, 2022
- Microsoft confirms they were hacked by Lapsus$ extortion group March 23, 2022
- White House Shares Checklist to Counter Russian Cyberattacks March 23, 2022
- Top Russian Meat Producer Hit With Windows BitLocker Encryption Attack March 23, 2022
- LAPSUS$ Hackers Claim to Have Breached Microsoft and Authentication Firm Okta March 23, 2022
- Android Password-Stealing Malware Infects 100,000 Google Play Users March 22, 2022
- Windows Zero-Day Flaw Giving Admin Rights Gets Unofficial Patch, Again March 22, 2022
- New Backdoor Targets French Entities via Open-Source Package Installer March 21, 2022
- 'CryptoRom' Crypto Scam Abusing iPhone Features to Target Mobile Users March 21, 2022
- Gh0stCringe RAT Targeting Database Servers in Recent Attacks March 20, 2022
- Western Digital Content App Vulnerable to Unauthorized Media Access March 20, 2022
- NCSC Launches Awareness Campaign to Strengthen Password Practices March 20, 2022
- FBI: Avoslocker Ransomware Targets US Critical Infrastructure March 19, 2022
- Agencies Warn on Satellite Hacks & GPS Jamming Affecting Airplanes, Critical Infrastructure March 19, 2022
- Hackers Target Bank Networks with new Rootkit to Steal Money from ATM Machines March 19, 2022
- Google: Chinese State Hackers Target Ukraine’s Government March 19, 2022
- This Week in Cyberspace (12-18 March 2022) March 18, 2022
Recent Comments
Archives
- September 2022 (1)
- May 2022 (2)
- March 2022 (50)
- February 2022 (56)
- January 2022 (119)
- December 2021 (34)


