
Researchers Uncover Hacker Group Behind Organized Financial-Theft Operation
Cybersecurity researchers have taken the wraps of an organized financial-theft operation undertaken by a discreet actor to target transaction processing systems and siphon funds from entities primarily located in Latin America for at least four years.
The malicious hacking group has been codenamed Elephant Beetle by Israeli incident response firm Sygnia, with the intrusions aimed at banks and retail companies by injecting fraudulent transactions among benign activity to slip under the radar after an extensive study of the targets' financial structures.
"The attack is relentless in its ingenious simplicity serving as an ideal tactic to hide in plain sight, without any need to develop exploits," the researchers said in a report shared with The Hacker News, calling out the group's overlaps with another tracked by Mandiant as FIN13, an "industrious" threat actor linked to data theft and ransomware attacks in Mexico stretching back as early as 2016.
Elephant Beetle is said to leverage an arsenal of no fewer than 80 unique tools and scripts to execute its attacks, while simultaneously taking steps to blend in with the victim's environment over long periods to achieve its objectives.
"The unique modus operandi associated with the Elephant Beetle is their deep research and knowledge of victim's financial systems and operations and their persistent search for vulnerable methods to technically inject financial transactions, ultimately leading to major financial theft," Arie Zilberstein, vice president of incident response at Sygnia, told The Hacker News. "Given the long period of persistence this group has in victim's networks, they often change and adapt their techniques and tooling to continue to be relevant."
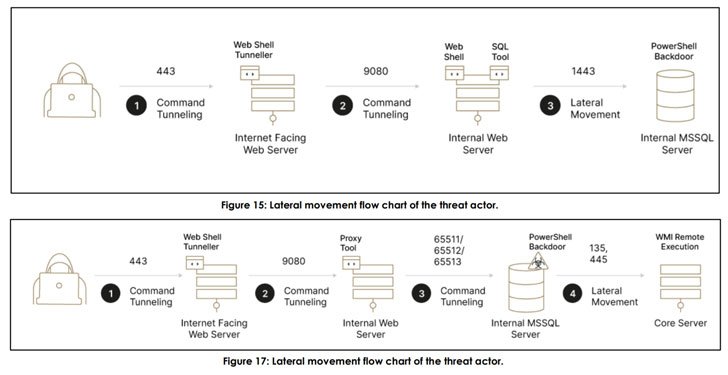
Zilberstein attributed the success of the campaign to the vast attack surface provided by legacy systems that are present in financial institutions' networks and can serve as entry points, thereby enabling attackers to gain a permanent foothold into target networks.
The adversary's modus operandi follows a low-profile pattern that begins with planting backdoors to study the victim's environment, specifically with an aim to understand the various processes used to facilitate financial transactions, followed by inserting rogue transactions of its own into the network that steal incremental amounts of money from the target to avoid setting off alarm.
But in the event the actor's fraudulent actions come to light, they temporarily cease their operations only to return a few months later. The initial access is brokered by taking advantage of unpatched flaws in external-facing Java-based web servers such as WebSphere and WebLogic, ultimately leading to the deployment of web shells that enable remote code execution and lateral movement —
- CVE-2017-1000486 (CVSS score: 9.8) - Primefaces Application Expression Language Injection
- CVE-2015-7450 (CVSS score: 9.8) - WebSphere Application Server SOAP Deserialization Exploit
- CVE-2010-5326 (CVSS score: 10.0) - SAP NetWeaver Invoker Servlet Exploit
- EDB-ID-24963 - SAP NetWeaver ConfigServlet Remote Code Execution
"This attack emphasizes once again that sophisticated attackers are sometimes lurking in networks for [a] long time," Zilberstein said. "While a lot of emphasis is given today to avoiding and preventing the imminent risk of ransomware, some other threat actors are still operating to stealthily proliferate themselves in networks to get a long term and steady financial gain."
"Organizations need to pay extra attention to these systems, particularly those which are externally facing, and perform patching and continuous hunting to prevent and detect attacks of similar nature," Zilberstein added.
Source: https://thehackernews.com/2022/01/researchers-uncover-hacker-group-behind.html
Sign up for the e-mail list to be informed about the developments in the cyber world and to be informed about the weekly newsletter.


