
Zimbra Zero-Day Vulnerability Actively Exploited to Steal Emails
A cross-site scripting (XSS) Zimbra security vulnerability is actively exploited in attacks targeting European media and government organizations.
Zimbra is an email and collaboration platform that also includes instant messaging, contacts, video conferencing, file sharing, and cloud storage capabilities., anlık mesajlaşma, kişiler, video konferans, dosya paylaşımı ve bulut depolama özelliklerini de içeren bir e-posta ve işbirliği platformudur.
According to Zimbra, more than 200,000 businesses from over 140 countries are using its software, including over 1,000 government and financial organizations.
Attacks linked to Chinese threat actor
"At the time of writing, this exploit has no available patch, nor has it been assigned a CVE (i.e., this is a zero-day vulnerability)," the researchers said.
"Volexity can confirm and has tested that the most recent versions of Zimbra—8.8.15 P29 & P30—remain vulnerable; testing of version 9.0.0 indicates it is likely unaffected."
Volexity says that so far, it only observed a single, previously unknown threat actor it tracks as TEMP_Heretic (believed to be Chinese) exploiting the zero-day in spear-phishing campaigns to steal emails.
However, the vulnerability can also enable attackers to perform other malicious actions "in the context of the user's Zimbra webmail session," including:
- exfiltrating cookies to allow persistent access to a mailbox
- sending phishing messages to the user's contacts
- displaying prompt to download malware from trusted websites
Zero-day exploited for email theft
"At the time of writing, this exploit has no available patch, nor has it been assigned a CVE (i.e., this is a zero-day vulnerability)," the researchers said.
"Volexity can confirm and has tested that the most recent versions of Zimbra—8.8.15 P29 & P30—remain vulnerable; testing of version 9.0.0 indicates it is likely unaffected."
Volexity says that so far, it only observed a single, previously unknown threat actor it tracks as TEMP_Heretic (believed to be Chinese) exploiting the zero-day in spear-phishing campaigns to steal emails.
The malicious code allowed the attackers to go through emails in the victims' mailboxes and exfiltrate email contents and attachments to attacker-controlled servers.
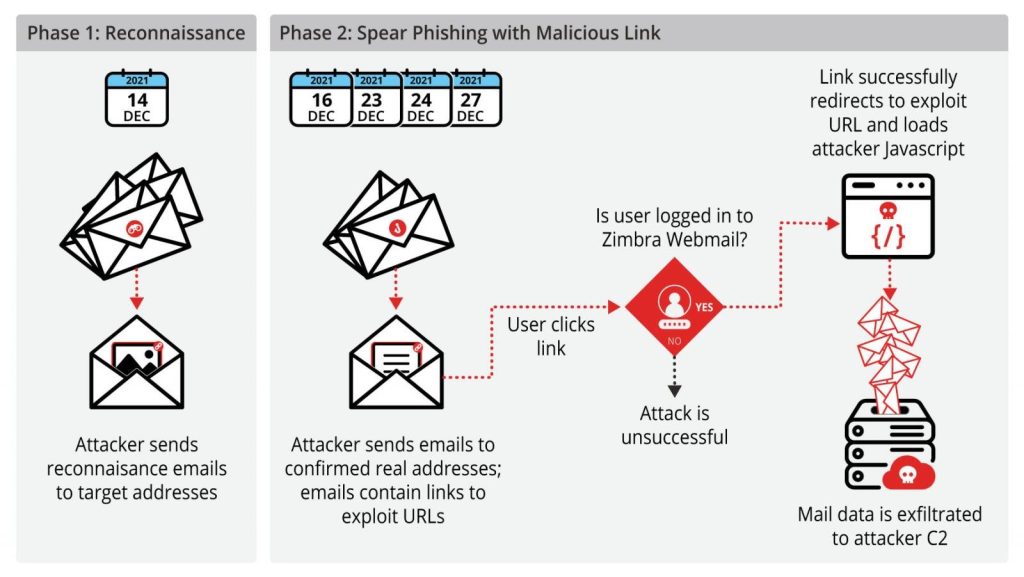
"At the time of this writing, there is no official patch or workaround for this vulnerability. Volexity has notified Zimbra of the exploit and hopes a patch will be available soon," the company said.
"Based on BinaryEdge data, approximately 33,000 servers are running the Zimbra email server, although the true number is likely to be higher."
Volexity recommends taking the following measures to block attacks exploiting this zero-day:
- All of the indicators here should be blocked at the mail gateway and network level
- Users of Zimbra should analyze historical referrer data for suspicious access and referrers. The default location for these logs can be found at /opt/zimbra/log/access*.log
- Users of Zimbra should consider upgrading to version 9.0.0, as there is currently no secure version of 8.8.15.
A disclosure timeline and indicators of compromise (IoCs), including domains and IP addresses linked to the campaign (dubbed EmailThief), are available at the end of the report Volexity published today.
Sign up for the e-mail list to be informed about the developments in the cyber world and to be informed about the weekly newsletter.


