
Google Project Zero: Vendors Are Now Quicker at Fixing Zero-Days
Google’s Project Zero has published a report showing that organizations took less time to address the zero-day vulnerabilities that the team reported last year.
As the data shows, the average period software vendors needed to issue security fixes reported by Project Zero last year was 52 days, down from 80 days three years ago.
Moreover, almost all vendors addressed the flaw within the standard industry deadline of 90 days, plus a grace period of two weeks.
Flaws you can't ignore
Zero-day vulnerabilities are security issues unknown to the software developer at the time of their discovery or are known but haven’t been patched.
They typically offer hackers a window of opportunity even after a patch becomes available because not everyone can fix the problem immediately.
As such, responding to zero-day vulnerability reports quickly is of utmost importance and it also demonstrates how serious software vendors are about the security of their products, how efficient they are with the development cycle.
For security analysts who discover them, the period of disclosure cannot be extended indefinitely, as there's always a chance they were not the first to find out about them.
The zero-day landscape
Project Zero'dan 376 sıfır gün bulgu ve raporuna dayanan 2019-2021 istatistiklerine göre, %26'sı Microsoft, %23'ü Apple ve %16'sı Google'ı ilgilendiriyor.
These three software giants account for 65% of the total findings, reflecting the complexity and high volume of their software products, inevitably creating gaps or dark spots for their otherwise crowded and capable security teams.
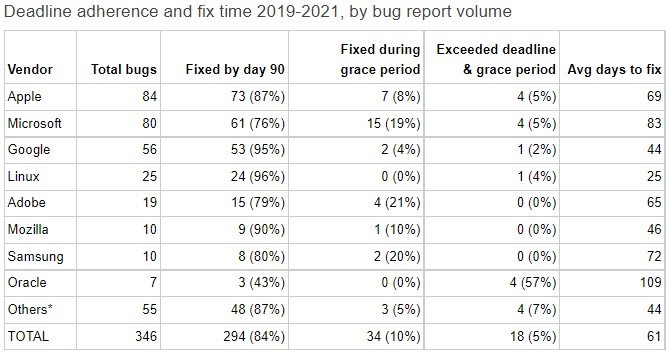
The best performers in terms of patching within the deadline were Linux, Mozilla, and Google, while the worst were Oracle, Microsoft, and Samsung. Microsoft also had the most fixes within the grace period, marginally pushing them right before they were made public.
In the highly competitive field of mobile OS, Google reports the same performance from both iOS and Android, with the former having an average fix time of 70 days, with the latter needing 72 days.
In the web browser category, Chrome beats everyone with an average bug-fixing period of 29.9 days, while Firefox comes second with 37.8 days.
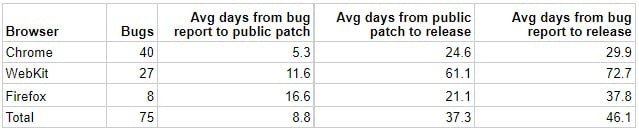
Apple took more than double that time to fix WebKit flaws, which have been plaguing Safari in the past couple of years, needing an average of 72.7 days.
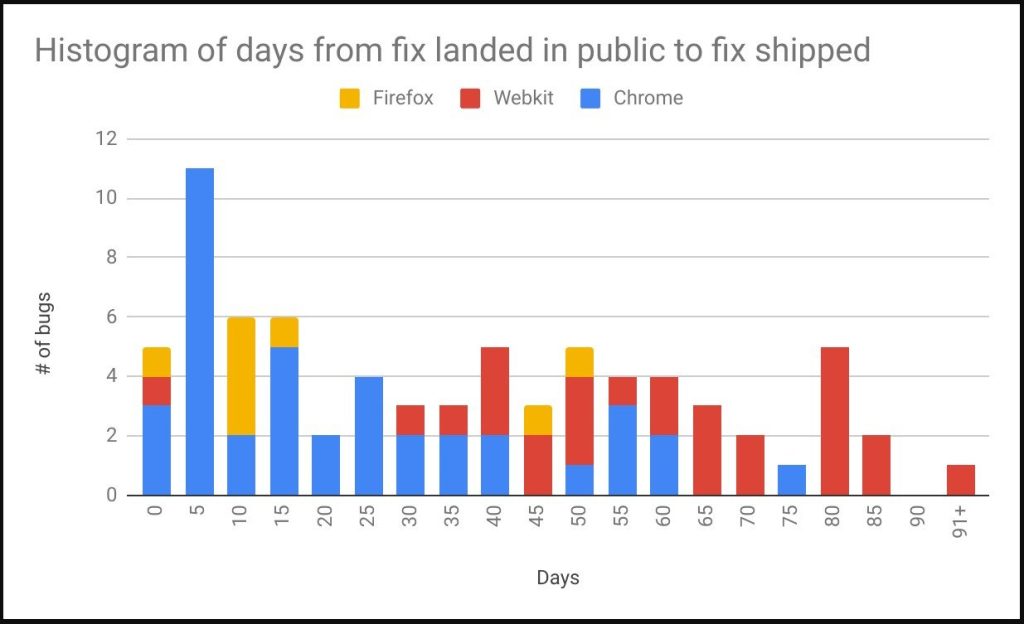
As Google’s Project Zero team comments in the report:
WebKit is the outlier in this analysis, with the longest number of days to release a patch at 73 days. Their time to land the fix publicly is in the middle between Chrome and Firefox, but unfortunately this leaves a very long amount of time for opportunistic attackers to find the patch and exploit it prior to the fix being made available to users.
In conclusion, Google's security analysts have recognized some clear marks of improvement, but vendors can and should do more in the future as adversaries are keeping an eye out for bug reports for a chance to find a new attack avenue.
Sign up for the e-mail list to be informed about the developments in the cyber world and to be informed about the weekly newsletter.


