Ukraine Recruits "IT Army" to Hack Russian Entities, Lists 31 Targets
Ukraine is recruiting a volunteer "IT army" of security researchers and hackers to conduct cyberattacks on thirty-one Russian entities, including government agencies, critical infrastructure, and banks.
Saturday afternoon, Ukraine's Minister for Digital Transformation Mykhaylo Fedorov announced that they need volunteer "digital talents" for an "IT Army" to conduct operational tasks against Russia on the cyber frontline.
We are creating an IT army. We need digital talents. All operational tasks will be given here: https://t.co/Ie4ESfxoSn. There will be tasks for everyone. We continue to fight on the cyber front. The first task is on the channel for cyber specialists.
— Mykhailo Fedorov (@FedorovMykhailo) February 26, 2022
Soon after, a Telegram channel created to organize the IT Army's operations released a list of Russian targets.
This list includes 31 targets, including Russian government agencies, government IP addresses, government storage devices and mail servers, three banks, large corporations supporting critical infrastructure, and even the popular Russian search engine and email portal, Yandex.
The IT Army came soon after the Defense Ministry began recruiting Ukraine's underground hacker community to assist in cyberattacks against Russia.
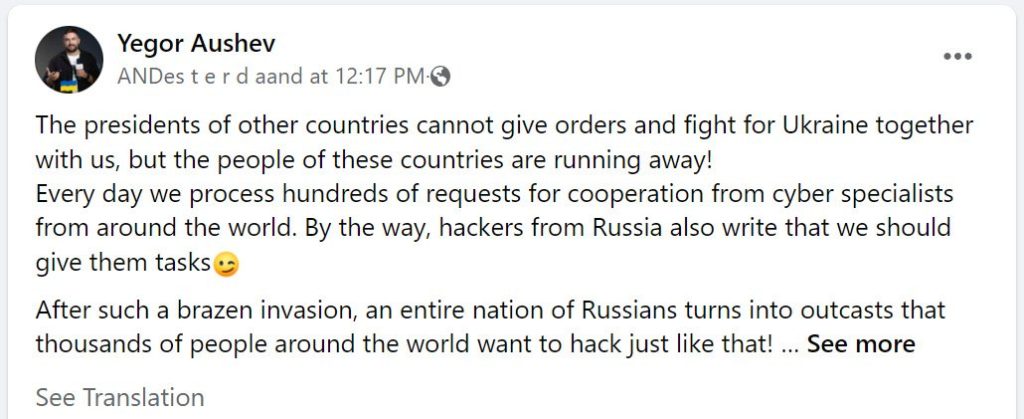
This call to action was published through Yegor Aushev, the founder of Cyber Unit Technologies, who shared an application form on Facebook.
Aushev claims that hackers worldwide have signed up to help Ukraine, even those from Russia.
The recruitment of volunteer hackers and security researchers appears to be having some effect on targeted sites.
Today, the Kremlin, State Duma, and Ministry of Defense websites were offline in what appears to be distributed denial of service attacks.
Should you join the IT Army?
While watching the images of Russia invading Ukraine unfold on TV or social media, you may be tempted to join the "IT army" and conduct cyberattacks against Russian entities.
However, it is important to remember that performing denial of service attacks, breaching networks and computers, and defacing websites is still illegal in most countries, regardless of the target.
Furthermore, as explained by Robert Lee, CEO of cybersecurity firm Dragos, many hands targeting the same entity could compromise legitimate law enforcement and government operations, and activities of cybersecurity companies who have legal agreements with the US government.
Anyone not working on behalf of a government having serious conversations about “hacking back” or launching cyber attacks against Russia please understand - respectfully - you’re an idiot and only going to make matters worse.
— Robert M. Lee (@RobertMLee) February 25, 2022
While governments aiding Ukraine may turn a blind eye to cyber activities targeting Russian entities, it is very important to think about the legal ramifications of conducting attacks before doing so.
The IT Army Telegram channel also suggests that people share videos of the attack on Ukraine on social media, YouTube, and through ads as another means of helping them during this conflict.
Sign up for the e-mail list to be informed about the developments in the cyber world and to be informed about the weekly newsletter.